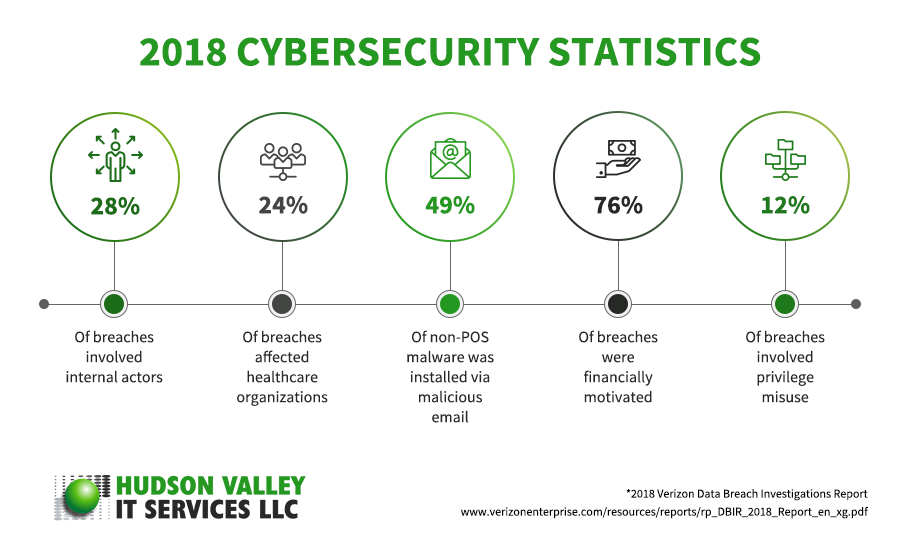
In the tech world, change is rapid. With cybersecurity, trends happen at an alarming rate. It’s always good to take a quick glance at the major facts and stats of 2018 for a better overview of the current state of cybersecurity, as well as an early warning of what may come.
[1] 90% of remote code execution attacks are associated with cryptomining
The big news back in 2017 was ransomware, thanks to WannaCry, Petya, and NotPetya. But by midyear, the attacks started to dwindle, and by December 2017, ransomware accounted for only 10% of online infections. What caused this huge drop? Cryptojacking.
Cryptojacking is using another person’s computer — often without the owner’s knowledge and permission — for cryptomining, which is part of the cryptocurrency process and is in itself not illegal. Why the sudden popularity? Holding data for ransom may get cybercriminals big bucks, but that depends on whether their victims pay up or not. With cryptojacking, these crooks can infect a lot of computers with bitcoin-mining software and stay undetected for longer periods, giving them larger yields.
Cryptojacking is a sneaky, unobtrusive, and illegal way to get rich, making it the top malware threat throughout 2018.
[2] 92% of malware is sent via email
When it comes to delivering malware through phishing attacks, the most popular method used by cybercriminals is still through email. Such attacks are becoming more targeted and increasingly sophisticated, so if you’re tired of reminding your staff to not indiscriminately click on just any email attachment, sorry, but you’ll need to continue doing so for 2019 — and maybe even beyond.
[3] 77% of attacks are from fileless malware
While email attacks remain a huge problem, another route is on the rise wherein hackers don’t need your email to infect your system with malware.
Introducing fileless malware — it uses your device's operating system and its tools for malicious activity. For example, cybercriminals will use either PowerShell or Windows Management Instrumentation (WMI) tools in Windows to execute their malicious commands like launch a ransomware attack or steal information.
Current antivirus software cannot detect fileless malware, making it a challenge to keep them off your systems. And while experts say next-generation security products will be able to detect fileless malware activity, preventing this new form of attack will be difficult.
[4] The average true cost of a ransomware attack is $5 million
Sometimes, management doesn’t truly comprehend the losses incurred from a ransomware attack. Even if it manages to avoid paying the ransom, a company still suffers losses such as staff overtime, lost revenues, and indirect costs due to downtime. Then there are costs for IT services, software, and other recovery-related costs. Tally them all up, and ransomware is a costly hit on revenues.
[5] It takes an average of 191 days to detect a data breach
It’s impossible for a company to prevent all attacks, so it’s important to have in place a system to identify if a breach has occurred as well as steps to repair the damage accordingly. In 2016, the average time it took organizations to identify a breach was 201 days. In 2017, the average was 191 days. It may not be much, but it’s certainly improving.
[6] More than 75% in the healthcare industry suffered a malware attack in 2018
The healthcare industry is a goldmine of data, given the high level of personal identifying information contained in patients’ records. And the large number of hospitals, medical treatment facilities, health insurance agencies, and healthcare manufacturing companies makes the industry a popular target for hackers.
[7] 61% have experienced a security incident involving their IoT systems
There are millions of Internet of Things (IoT) devices deployed out there, and cybercriminals have begun targeting them. In a 2018 survey, 64% of the respondents reported to have already deployed IoT devices, and 20% said they’ll add more within this year. But in the same survey, 28% said they consider IoT security “very important”. The majority said it was somewhat important, or not important at all. This disturbing attitude means we will see a rise in IoT attacks in the coming year.
When it comes to cybersecurity, it’s better to partner with a managed services provider (MSP) like Hudson Valley IT Services. Our experts will help protect your organization from the ever-increasing security threats that can cripple or put companies out of business. If you’re a small- or medium-sized business needing cybersecurity, we’re the MSP for you. We can also assist you with data backup and disaster recovery, compliance, cloud services, and more. Call or send us a message today; we’d love to hear from you.
Like This Article?
Sign up below and once a month we'll send you a roundup of our most popular posts