Bad habits are a very real part of life; even organizations can be plagued by them. Like people, it’s all too easy for enterprises who aren’t vigilant to fall into comfortable patterns that are detrimental to the business. The case can be said for security measures that give a false sense of protection but actually increase the risk of a data breach.
Without realizing it, companies can put their data at risk with the kind of security they’ve grown accustomed to. Your organization may be one of them. Here’s a list to help you recognize, avoid, and correct bad security habits that put your business in harm’s way.
Lacking a strong password policy
While new threats and security technologies emerge, passwords firmly remain an essential security measure. However, if your organization is not careful, passwords can make it easy for malicious actors to compromise your accounts and steal your data.
Reusing passwords across multiple personal and professional accounts, as well as changing passwords infrequently, is one of those habits that make it easy for hackers to steal data. Changing passwords multiple times a year or using many different passwords can be an inconvenience, but once one account is compromised, other accounts are likely to follow.
It’s a cringe-worthy moment realizing that people still use passwords like “sunshine” or “123456” for accounts containing confidential information. Not only are they weak, but these passwords are also susceptible to brute force attacks. They’re practically useless to protect data from a serious attack. As a response, organizations should diligently enforce strong password policies or reevaluate them if employees continue to use weak passwords.
securing mobile devices
Mobile devices for work have become ubiquitous. The mobility, scalability, and flexibility they bring to productivity have made them a necessity. Whether sanctioned by an organization or not, workers are using devices to access and store confidential business data.
Download our free eBook!
Cybersecurity can be tricky and expensive. Our free eBook, 3 Essential types of cyber security solutions your business must have will help you understand just enough to make the right call when it comes time to decide how to make everything work with the budget.
Devices such as smartphones can easily be lost or stolen and can be used to gain access to an organization’s network and data. An organization that doesn’t help secure these devices from tampering nor implement policies to secure business data is courting disaster.
Transmitting unencrypted data on unsecured networks
It’s not uncommon for employees to use free or public Wi-Fi to get some work done outside of the office. Using these unsecured wireless connections to load or transfer unencrypted work data is dangerous because hackers can intercept the data.
Meanwhile, some businesses still use unsecured networks at their offices, seemingly oblivious of the risk of a data breach this poses. It may seem more cost-effective to leave traffic for guest users unencrypted or cheaper to leave an entire network unsecured. But both are security holes that a hacker can exploit.
Neglecting updates or postponing patches
Patching or updating is a notorious inconvenience not only for the wait it causes but also for its potential to disrupt productivity. However, hardware and software developers are constantly developing and releasing updates to address vulnerabilities that compromise a network. Organizations can’t neglect them and have to find ways to prioritize and schedule these security solutions around work.
Thinking you’re not a target
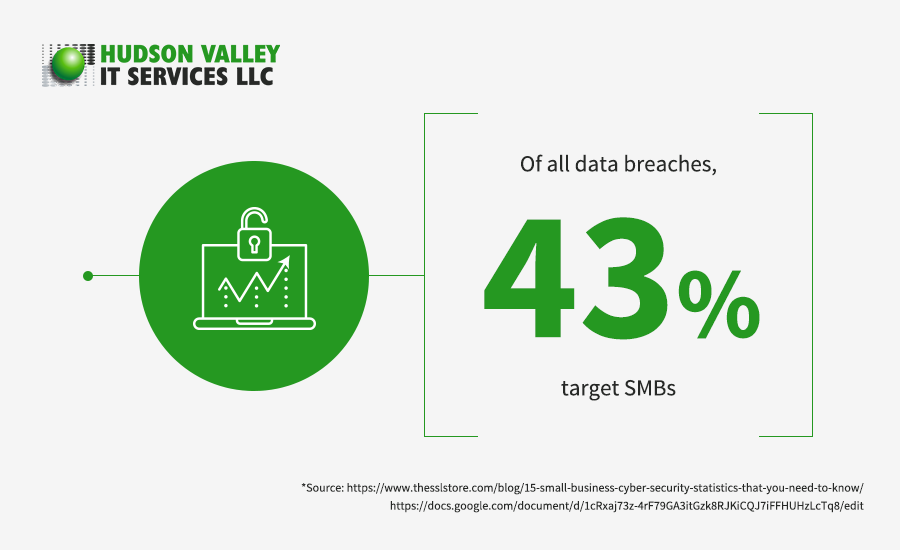
43% of all data breaches target small- and medium-sized businesses (SMBs). Yet it’s not uncommon for SMBs to think that they are too small to be a target for data breaches. Because of this mindset, SMBs are neither equipped nor up to date with their security.
Some of these businesses try to get by on bare minimum security. They adopt basic security solutions such as firewalls and anti-malware, but they do so without further assessment of their specific risk profile. These security measures will easily be overcome by more sophisticated and emergent threats.
Because these SMBs don’t take security seriously, they have it at the bottom of their budget priorities. So when a data breach does happen, the fallout can be devastating. The cost of a data breach continues to rise, and today a data breach can cost the average business up to $3.92 million.
Relying on an email client’s built-in security
According to Mimecast’s 2019 the State of Email Security, cybercriminals continue to use email as a primary vehicle to steal data and deliver advanced threats. Your organization’s top business communications channel remains your biggest vulnerability and security risk.
Your business can’t rely on the built-in security of an email client. Employees should be trained to recognize email security risks and red flags to mitigate the danger of a data breach via email. Strong email protection measures such as malware scanning and anti-phishing technology should also be implemented.
The security decisions you make today will determine your organization’s safety and resilience for years to come. With Hudson Valley IT Services’ comprehensive security consulting services, you can feel more confident about the actions you take to protect your business, reputation, employees, customers, facilities, and assets. Talk to us today.



